X:/Anonymous
This is a self-hosted, open-source, end-to-end encrypted chat application that doesn't save conversations. Basically, when you create a conversation, a private and public key pair is generated locally on your browser. Nobody else (including the server) knows what the private key is. When you send messages to the other person using X:/Anonymous, the message is encrypted using RSA (the key size is up to the user, they can choose 2048, 3072, or 4096. The bigger the key size, the longer their messages can be, but the service will be slower). Conversations are stored locally as well, so the server literally saves no information about you by design. Glitch, the website I mention in the GitHub repo (accessed through the download button at the end of this page), is used to host the application. It probably stores IP addresses and whatnot, but they never ever get a plaintext copy of your messages. They don't get your private key at any point either. So the server ultimately has absolutely no idea what's actually being said between two people, and since it's self hosted, you can know for sure that there isn't any malicious code or anything that could compromise the security of your communications.
Pretty much every social media platform has a chat feature, but they all store your chats in such a way that they can read them. This is a massive invasion of privacy. What if you want to share a secret with one person, and one person only? Wouldn't you feel better knowing potentially hundreds of people don't have access to your conversations? That's why I created X:/Anonymous.
How it works:
Let's suppose there are two people who want to talk to each other, but what they want to say has to remain an absolute secret, to the point where they don't even want a record of the conversation existing. We'll call them Adam and Eve. Adam creates an anonymous conversation using X:/Anonymous. On his browser, completely on the client-side, a public key and private key are generated for him. He sends his public key to the server, and gets an anonymous ID generated for him. A file is created on the server that contains the time at which the conversation was created, when it was last modified, and Adam's anonymous ID and public key. A conversation ID is also generated, and Adam is redirected to the chat page. He can now send a link for Eve to join by sharing his URL. Eve clicks on the link, and she (still on the client-side) gets a private and public key pair generated for her, is given an anonymous ID, and is given access to the chat page. Adam and Eve's private keys are stored on their browser's local storage, never by the server. When they send a message to each other, they encrypt their messages with the other person's public key. The encrypted message is sent to the server, and relayed to the other person, who then decrypts it locally on the client-side with their private key. At no point does the server have access to any private keys, or any plaintext data. Messages that are sent and received also get stored in the browser's local storage. The downside is that there's no way to really prove what the original content of a message was if one of the users decides to modify their local storage records and make it seem like the other person said something they didn't. But would you rather trust one other person (who's potentially a friend), or an entire company that would have a lot to gain from selling your data?
 The image above shows the landing/home page of the website. The user can access my GitHub, create a conversation, or change certain settings.
The image above shows the landing/home page of the website. The user can access my GitHub, create a conversation, or change certain settings.
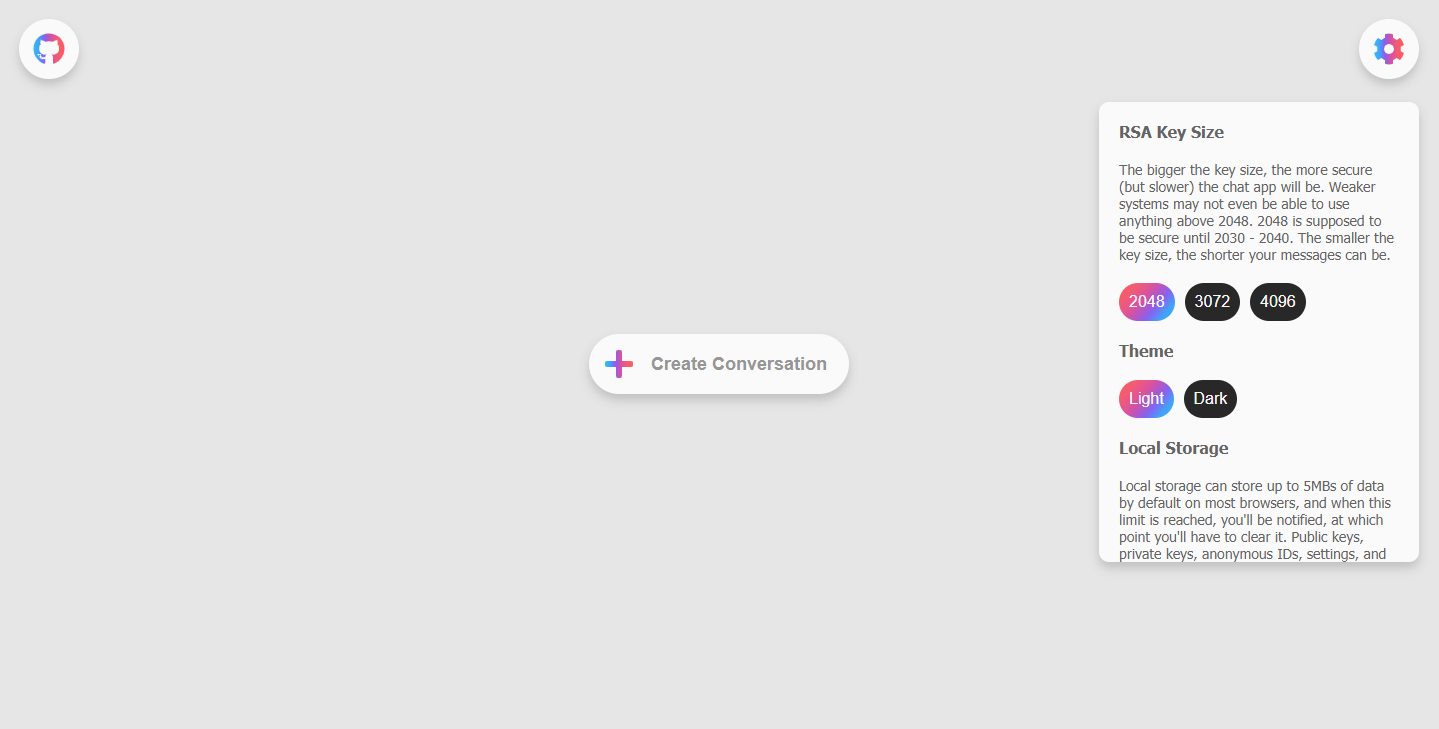 Through the settings pane, they can change the RSA key size, the website's theme, and they can also see how full their browser's local storage is, and empty it if need be.
Through the settings pane, they can change the RSA key size, the website's theme, and they can also see how full their browser's local storage is, and empty it if need be.
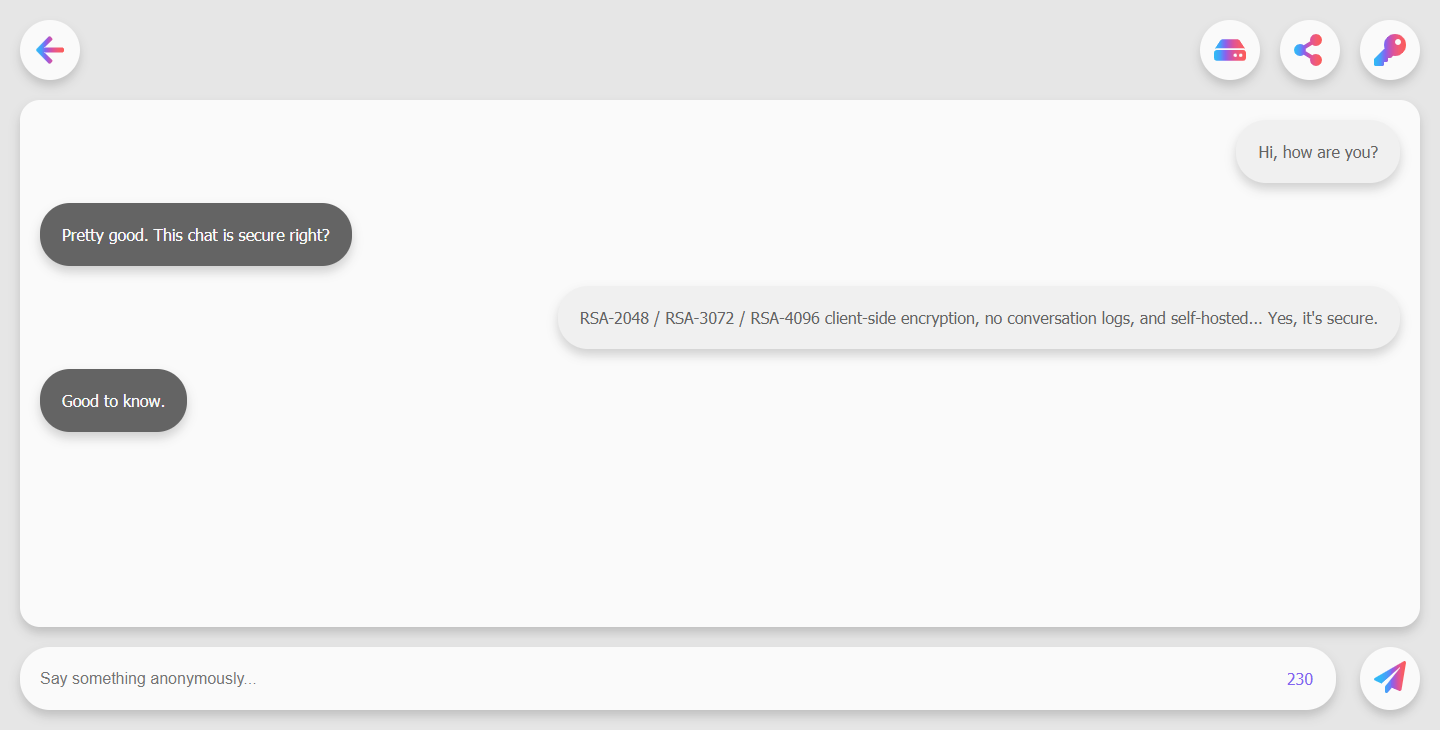 This image shows the main chat page. There is a back button to go back to the home page and create another conversation, a drive button that tells the user how much free space they have in their local storage, there's also a share button that copies the current URL to the user's clipboard, and finally a key button that shows the user's anonymous ID, public key, private key, and the other user's public key.
This image shows the main chat page. There is a back button to go back to the home page and create another conversation, a drive button that tells the user how much free space they have in their local storage, there's also a share button that copies the current URL to the user's clipboard, and finally a key button that shows the user's anonymous ID, public key, private key, and the other user's public key.
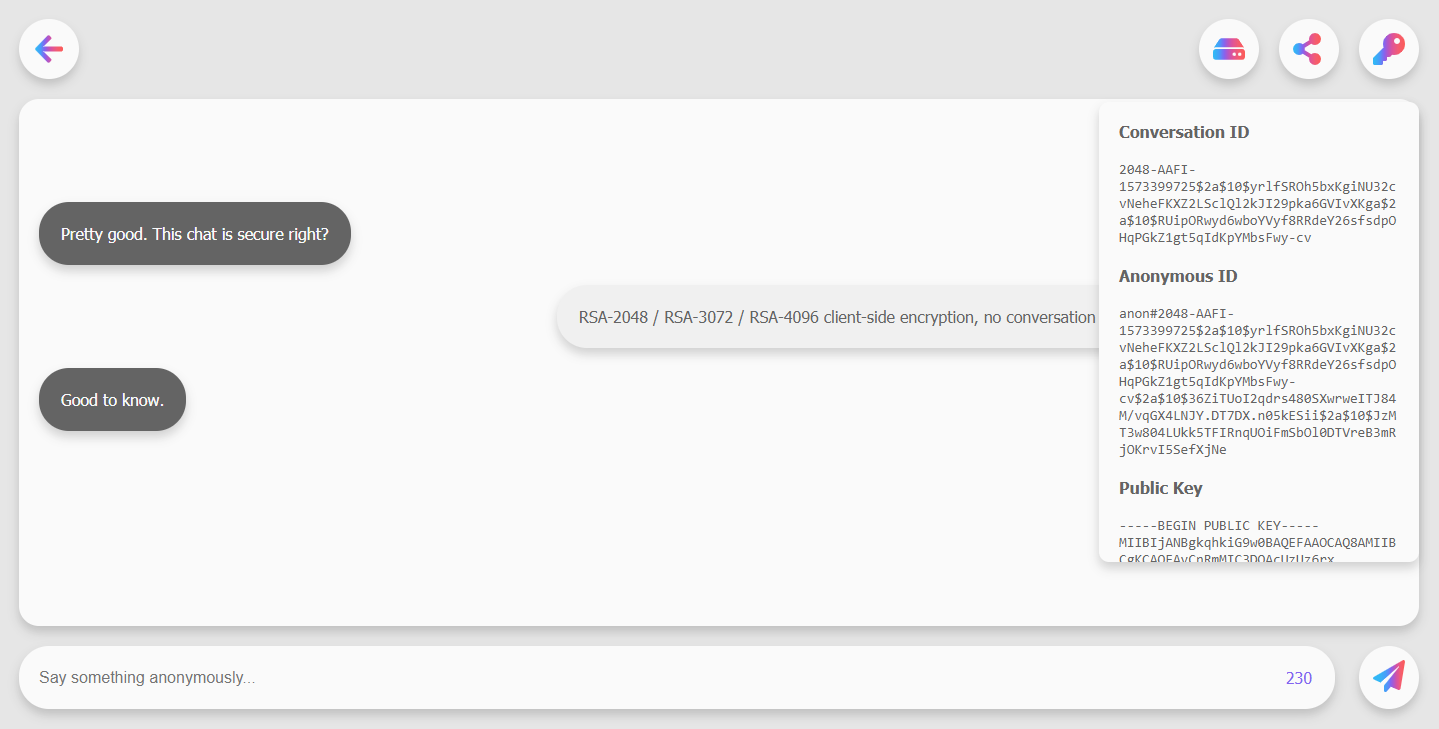 The image above shows the pane that opens if the user clicks on the key icon.
The image above shows the pane that opens if the user clicks on the key icon.
 The website also has a dark theme as shown above.
The website also has a dark theme as shown above.
 The image above shows the landing/home page of the website. The user can access my GitHub, create a conversation, or change certain settings.
The image above shows the landing/home page of the website. The user can access my GitHub, create a conversation, or change certain settings.
 Through the settings pane, they can change the RSA key size, the website's theme, and they can also see how full their browser's local storage is, and empty it if need be.
Through the settings pane, they can change the RSA key size, the website's theme, and they can also see how full their browser's local storage is, and empty it if need be.
 This image shows the main chat page. There is a back button to go back to the home page and create another conversation, a drive button that tells the user how much free space they have in their local storage, there's also a share button that copies the current URL to the user's clipboard, and finally a key button that shows the user's anonymous ID, public key, private key, and the other user's public key.
This image shows the main chat page. There is a back button to go back to the home page and create another conversation, a drive button that tells the user how much free space they have in their local storage, there's also a share button that copies the current URL to the user's clipboard, and finally a key button that shows the user's anonymous ID, public key, private key, and the other user's public key.
 The image above shows the pane that opens if the user clicks on the key icon.
The image above shows the pane that opens if the user clicks on the key icon.
 The website also has a dark theme as shown above.
The website also has a dark theme as shown above.